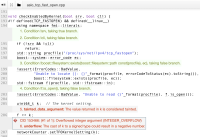
Overflowed integer argument
The argument will be too small or even negative, likely resulting in unexpected behavior (for example, under-allocation in a memory allocation function). An integer overflow occurs, with the overflowed value used as an argument to a function
/src/mongo/transport/asio/asio_tcp_fast_open.cpp:206: INTEGER_OVERFLOW 153466 The value returned in "k" is considered tainted.
/src/mongo/transport/asio/asio_tcp_fast_open.cpp:207: INTEGER_OVERFLOW 153466 The cast of "k" to a signed type could result in a negative number.