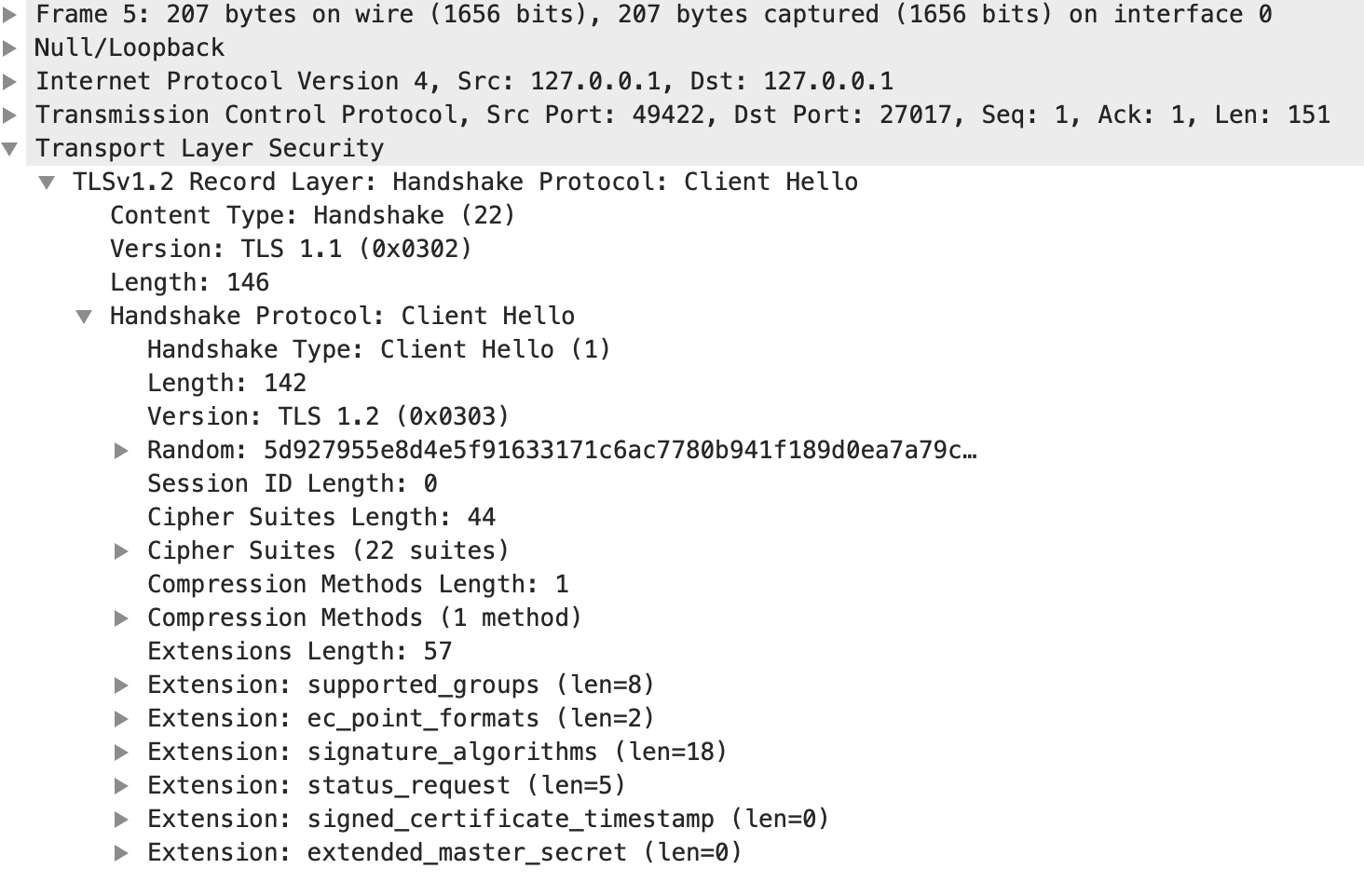
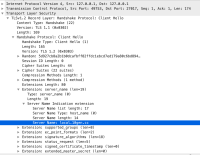
Because of the way Apple's TLS library works, we have no direct way of manually setting or disabling the TLS SNI extension separately from the PeerDomainName in our usage of SSLSetPeerDomainName.
Because of this, Apple's TLS library will naively advertise an IP address as an SNI name if it is provided as the PeerDomainName. This is against the TLS spec per RFC 6066, Section 3. We removed the advertisement of IP addresses in the SNI extension in SERVER-42287 and SERVER-43234.
However, when allowInvalidHostnames is enabled, the PeerDomainName is cleared, and SNI is not advertised, which causes test failure and potentially confusion for anything that needs to use the SNI for whatever reason.